Voting Machines
...over the past twenty years, we have let corporations into our polling places, locations so sacred to democracy that in many states even international election monitors and reporters are banned. With the implementation of "black box voting" (the use of electronic voting machines), these corporations are recording our votes, compiling and tabulating them, and then telling us the total numbers - and doing it all using "proprietary" hardware and software that we cannot observe, cannot audit, and cannot control. If the vote-counting corporation says candidate X or candidate Y won the vote, we have no means of rebutting that, and they have no way of proving it. We're asked simply to trust them. From Thom Hartman's book Threshold pg 210.

Paperless electronic voting machines "cannot be made secure," according to draft recommendations issued by NIST that advises the U.S. Election Assistance Commission.
Voting machines are uncertified, unstandardized, often produce no audit trail, and are made by hard right-wing Republicans. The US is probably the only country in which election infrastructure is in the hands of private partisans.
As if that were not enough of a problem, the source code for these machines is proprietary and is protected as a trade secret, so it is not available for audit. By accident, some of it leaked out (Diebold's web site was not secured.)
See Richard Stallman's comments.

Best 10 Free and Open Source Voting Software Solutions
Election Security: When to Worry, When to Not, and the Takeaway from Antrim County, Michigan (11/10/2020)
America faces a voting security crisis in 2020. Here’s why – and what officials can do about it. (8/16/2019)
http://www.votersunite.org/electionproblems.asp;
voteirv.org Instant Runoff Voting a prerequisite to break the two party monopoly of US elections.
BlackBoxVoting to File Anti-Trust Complaint against ES&S/Diebold merger
Diebold has a "Delete" button for erasing audit logs (3/3/2009)
Sign the petition for independent inspection of voting machines in the US.
Mitch McConnell received donations from voting machine company lobbyists before blocking election security bills https://t.co/3KfBB7HEpF
— Muckmaker™ (@RealMuckmaker) September 1, 2019
For years, Ds wondered why Rs kept sweeping the county races in Shelby County, TN. It turned out that the county's ES&S voting system was "dropping" votes from predominantly black precincts. Former election commissioner Norma Lester (below) has the scoop. https://t.co/ILZEkHY7oS
— Jennifer Cohn ✍🏻 (@jennycohn1) June 23, 2020
A note from Bruce Schneier.
Mitch McConnell Received Donations from Voting Machine Lobbyists Before Blocking Election Security Bills (7/26/2019)
Rs seem to want to put only Dominion Voting out of business, which wld give America’s largest & arguably most problematic voting machine vendor (ES&S) even more control over elections. I compiled these facts about ES&S to try to help realign the narrative. https://t.co/eKjotYTXxD
— Jennifer Cohn ✍🏻 📢 (@jennycohn1) December 27, 2020
About Voting Machines and the American Taliban (7/2018)
Top-Secret NSA Report Details Russian Hacking Effort Days Before 2016 Election (6/5/2017)
Sen. Marsha Blackburn (R), who personally blocked federal election-security legislation, is from TN. TN’s largest county is Shelby County where, in 2015, Bloomberg reported that voting machines in predominantly black precincts were losing black votes. 1/ https://t.co/XL13Zc0T2k
— Jennifer Cohn ✍🏻 (@jennycohn1) April 20, 2020
One problem is that the tabulation software is "proprietary." A private company owns the code to the count—and the privateers will fight fiercely, with GOP help, to keep the ballot counting code their commercial secret. Greg Palast (12/1/2016)
Public outrage should be through the roof right now, but instead we watch Democracy die a slow death.
— Political Mac 11 (@MackPolitical) August 26, 2021
☎️ Congress and keep the pressure on them!
It is just as important to protect voting rights and our votes across the U.S. as it is to prosecute the #TrumpCoup ringleaders.
🧵 https://t.co/900FsNh8tE pic.twitter.com/HMypUhHi63
What to Do When Voting Machines Fail (11/5/2018)
San Francisco funds open source voting (6/2/2016)
Los Angeles County voting to shift from inkblots to open source (6/13/2015)
My PSA about these new touchscreen voting machines (universal use ballot marking devices), which many jurisdictions have chosen in lieu of unhackable #HandMarkedPaperBallots. https://t.co/zLtavpwvDB
— Jennifer Cohn ✍🏻 (@jennycohn1) February 25, 2020
Old,
faulty voting machines put US democracy at risk, report warns (9/15/2015)
How
to Rig An Election (11/2012 Harper's Magazine)
Romney
ties to Voting Machine Co (10/23/2012)
Cutting Through Hype, Hypocrisy In Voter Fraud Claims
Accessibility and Auditability in Electronic Voting (5/17/2004)
Online Policy Group v. Diebold (2004)
Computer Voting Is Open To Easy Fraud (12/23/3)
The inexplicable 127k undervotes in the 2018 GA Lt. Governor’s race “seemed to specifically happen in black neighborhoods. Even stranger, the black voters’ absentee mail ballots didn’t reflect the drop-off..”
— Jennifer Cohn ✍🏻 (@jennycohn1) September 30, 2019
ES&S has the GA contract too! #gapol https://t.co/25on1yEMHx 2/
Georgia Havoc on Pricey Voting Machines
— SNOWFLAKE (@jawja100) June 13, 2020
WE WERE WARNED!!!
GOP HELL BENT TO PAY OVER $100M FOR THESE MACHINES, PLUS CONTRACT TO BUY OVERPRICED PAPER & PENN & WHAT ELSE?
CONSERVATIVE ABT $ 4 INFRASTRUCTURE, HEALTH, EDUCATION
✅$$$ TO STEAL AN ELECTION!https://t.co/aiYgj4x9lW
From the Election Defense Alliance
- U.S. elections have been outsourced to (highly partisan) private corporations.
- Every study (from Princeton to GAO) concurs that computerized voting is extremely vulnerable to manipulation.
- Polling methodology has already morphed to account for consistent "red shifts" in election results, so the polls mirror the elections and everything looks consistent.
- Ever wonder why voters seem to be voting against
their own interests, the Progressive agenda is DOA, and America looks
to be veering further and further Right ?
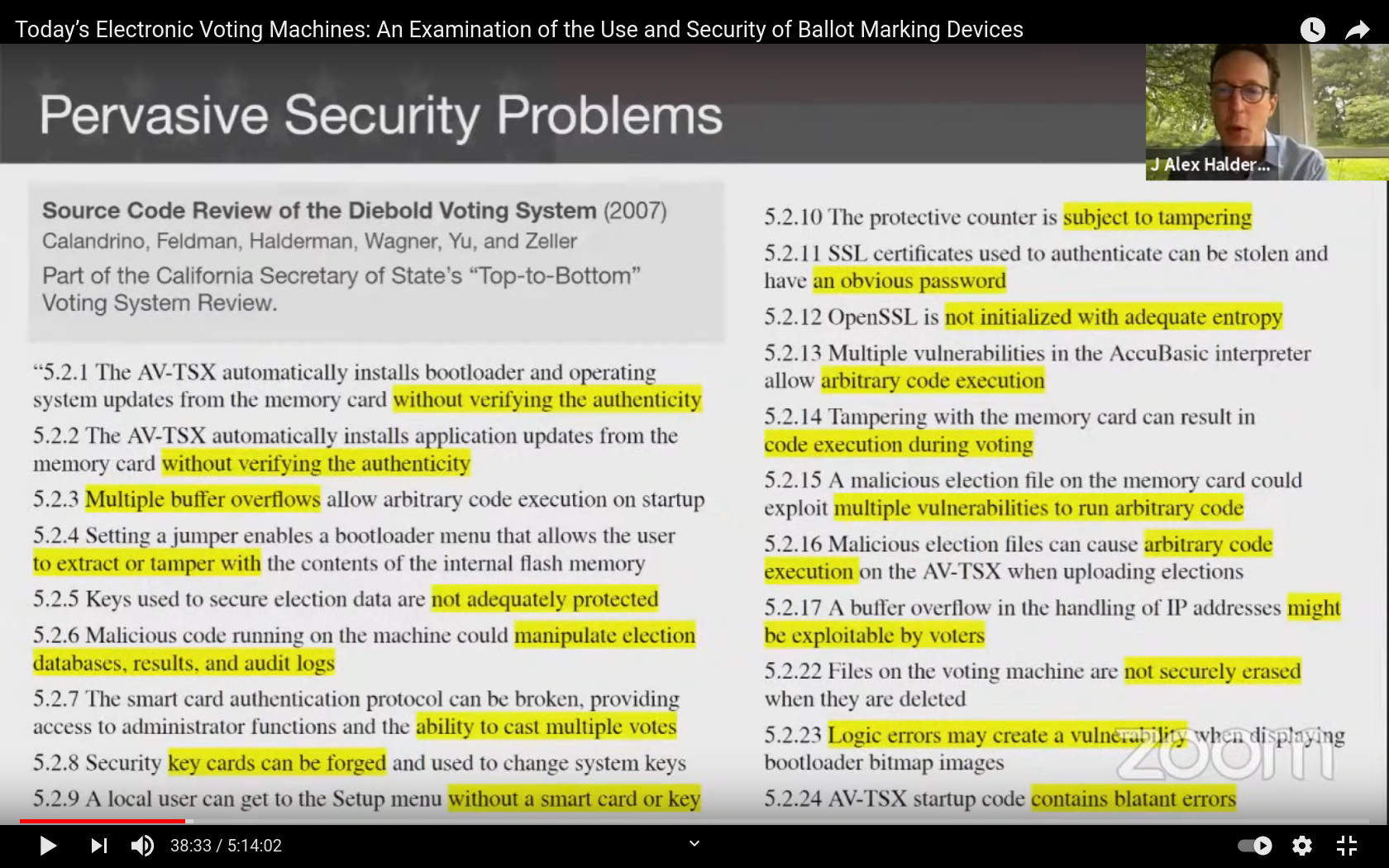
Diebold Source Code!!! --by ouranos (dailykos.com) "Dr. Avi Rubin is currently Professor of Computer Science at John Hopkins University. He 'accidentally' got his hands on a copy of the Diebold software program--Diebold's source code--which runs their e-voting machines. Dr. Rubin's students pored over 48,609 lines of code that make up this software. One line in particular stood out over all the rest: #defineDESKEY((des_KEY8F2654hd4" All commercial programs have provisions to be encrypted so as to protect them from having their contents read or changed by anyone not having the key... The line that staggered the Hopkins team was that the method used to encrypt the Diebold machines was a method called Digital Encryption Standard (DES), a code that was broken in 1997 and is NO LONGER USED by anyone to secure programs. F2654hd4 was the key to the encryption. Moreover, because the KEY was IN the source code, all Diebold machines would respond to the same key. Unlock one, you have then ALL unlocked. I can't believe there is a person alive who wouldn't understand the reason this was allowed to happen. This wasn't a mistake by any stretch of the imagination."
A warning. (excerpt follows)
"On May 6, 2007 the House Administration Committee reported out a modified bill called HR 811, also known as the Holt bill. In that bill's markup in committee, it got better and it got worse in various particulars, if you follow the debate. One way in which it got much worse is that instead of source code for the computer that would be given away for any citizen's inspection, they committee put in language that made the source code a government-recognized trade secret, available only to "qualified" experts, and then only if a strict nondisclosure agreement is signed that incorporates trade secrecy laws of the states, which almost always contain harsh punitive damages and attorneys fees clauses for violating the secrecy.
This language is particularly ominous. I know of no time before that an American legislative body has ever tried to pass law to reinforce secret vote counting. Of course, having a copy of the source code does not tell us if that code is the same as what's used on election day, nor does it tell us what the actual voting computers are asked to do on election day. It would be, of course, illegal for the software to differ, but it is readily possible to conceal a double Trojan Horse, for example, such that it is highly resistant to being found. It is not possible to verify that a piece of software remains unchanged, if it were, the problem of viruses would be solved since each program could self-verify whether or not it had been changed. As stated in the classic computer paper "Reflections on Trusting Trust" the only code you can trust is the code you wrote yourself and know nobody else has accessed."
Open Voting Foundation supports solutions for open voting. These solutions include software using open standard specifications that can be inspected by the public for flaws and even improved by the public. The software must also capture and count votes in ways that the voter can verify individually and would be statistically impossible to tamper with on any significant scale.
Hacking the Vote
Clinton Curtis testimony on elections before the Judiciary Committee.