Internet
"Concentration of technology is a surprising outcome of cheap hardware and free software. We could have had a world of peers. Instead, the net we built is the net we didn't want. We're in an age of surveillance with centralized control. We're in a world, which encourages swiping, clicking, and flame throwing." Eban Moglen
"But while we were having fun, we happily and willingly helped to create the greatest surveillance system ever imagined, a web whose strings give governments and businesses countless threads to pull, which makes us…puppets. The free flow of information over the Internet (except in places where that flow is blocked), which serves us well, may serve others better. Whether this distinction turns out to matter may be the one piece of information the Internet cannot deliver." Sue Halpern
Noospheric Consciousness
Integrating Neural Models of Consciousness and of the Web
Shima Beigi (2021)
Pushback Mounts Over Trump Administration ‘Termination’ of Digital Equity Law (5/22/2025)
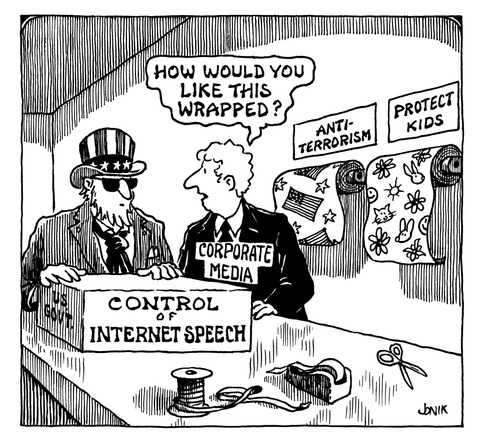
Congress Takes Another Step Toward Enabling Broad Internet Censorship (4/10/2025)
Elon Musk is out of control. Here is how to rein him in Robert Reich (8/30/2024)
FCC votes to restore net neutrality (4/25/2024)
Technofeudalism: What Killed Capitalism by Yanis Varoufakis (10/30/2023))
The internet, molded by deregulated, increasingly concentrated corporations and the unaccountable national security state, is turning into a panopticon. It knows where you are, what you are doing at all times. But it is not just an invasive snoop, It has been as commercialized as other media. Against public opinion, the Republican FCC removed net neutrality.
Initially, the peer-to-peer nature of the internet made it
democratic, but there are strong forces working to centralize and dominate it.
Search services require central infrastructure, and so does social
media like Facebook, Twitter, or Google.
Links
PrivacyInformation
Technology
Media
Free Software
National Security State
EFF
EPIC
most-visited websites
Center for Digital Hate
General Data Protection Regulation
Bruce Schneier
re Facebook - Cambridge Analytica
Fight for the Future
Save Internet Privacy
Mastodon (alternative to Twitter)
Search Quant
Digital Platform Act
Section 230
Secure Private Email
Radical Servers
Hosting Services
Webpy
Securing Your Home Router (video)
A Contract For the Web
Web Foundation
Mozilla Manifesto
TOR
TAILS
Freedom Box
Radical Servers
Hacker News
Freenet
edonkey
APC
OpenMedia.org
Freedom House
Digital Liberties
Public Knowledge
Ranking Digital Rights
Ranking Digital Rights
Battle For the Net
GoDaddy Ripoff Reports
PeerTube (alternative to Yutube.)
ActivityPub
OTR
OpenStandard
Most useful websites
Panopticlick.org
MayFirst
Techdirt
Meshed Insights
Center for Humane Technology
BuggedPlanet.info
Save the Internet
Mozilla Manifesto
Decide The Future
Fight For The Future
Data Central
IP Watch
Battle For The Net
Safe Harbor
Global Internet Liberty Campaign
Malware
Demand Progress
Citizen Lab
Netgain Partnership
VUPEN
FinFisher
OpenITP (Open Internet Tools Project)
2600
Open Wireless
Tow Center For Digital Journalism
Access
Charter of Human Rights and Principles for the Internet
Digital Freedom FoundationAmerican Censorship
Google Transparency ReportGlobal Network Initiative
Digital Imprimatur
Search Engine Land
BoingBoing (Corey Doctorow)
Toad.com (John Gilmore's page)

Join the Blue Ribbon Online Free Speech Campaign! Email: Tutanota or ProtonMail?
ProtonVPN
OMEMO
- Open Net Initiative
- Berkman Center at Harvard Law School
- Global Voices
- Burbank Digest
- WWW Virtual Library
- Internet Archive
- An Atlas of Cyberspaces
- An Atlas of Cyberspaces - Conceptual Maps
- Internet and Usenet Personal Security Site
- Portswigger
- Craig Samson
- Register.com
- Sascha Meinrath
- Open Compute Project
- Drumbeat
- StumbleUpon
- Recode
- Web Hosting Services
Cloud Storage
Pogoplugapps
OpenWatchCop Recorder
"In 2010, ’ co-founder Rebecca MacKinnon coined the term “networked authoritarianism” to define how China manipulates the internet to maintain power. The approach allows for limited debate around some issues but controls the platforms and frames the narratives up for discussion. Technology facilitates surveillance and social controls, and information, discussion, and activism with the potential to threaten power is forbidden."
The First Amendment assures your right of free speech, but that really does not apply to the internet. After all, the internet is private, and providers are free to decide what you can say, or if you can be there at all. Now there is a small army of censors who decide if you say something they don´t like. Facebook is used by news organizations to police comments on their web sites.
I happen to think that Republicans are cult followers of an authoritarian leader who regularly lies, dismantles government institutions, attacks democracy, expands the military and the nuclear arsenal, aligns with other authoritarians, cuts taxes for the wealthy, proposes budget cuts for social welfare programs, wants to repeal healthcare with no replacement. We have a right-wing government with all of the characteristics of a Fascist state, racism, human rights abuse, and empire included.
You are better off with free software and a Tor box, but there probably is no longer any real escape. The Fourth Amendment is pretty much dead.
EU: Digital Services Act: regulating platforms for a safer online space for users (1/20/2022)
Internet freedom on the decline in US and globally, study finds (9/21/2021)
Facebook Stopped Employees From Reading An Internal Report About Its Role In The Insurrection. You Can Read It Here.
The Simplest Way to Rein In Facebook and Big Tech (3/29/2021)
The Antitrust Case Against Big Tech, Shaped by Tech Industry Exiles (12/20/2020)
How to Destroy Surveillance Capitalism (11/17/2020)
Freedom on the Net 2019, The Crisis of Social Media
How to Declutter Your Digital World (9/15/2020)
New Trump Appointee Puts Global Internet Freedom at Risk, Critics Say (7/4/2020)
I Invented the World Wide Web. Here’s How We Can Fix It. (11/24/2019)
Big Business Is Overcharging You $5,000 a Year (11/10/2019)
Trump, Zuckerberg & Pals Are Breaking America (10/29/2019)
The Republican political operatives who call the shots at Facebook (10/17/2019)
Portland Is Again Blazing Trails for Open Internet Access
Put the internet back under your control with the FreedomBox (4/22/2019)
Facebook Is a Social Menace (1/10/2019)
The privacy risks of smart speakers like Amazon Echo, Apple HomePod, and Google Home (1/10/2019)
Shadow Regulation
Broadband industry groups sue California over net neutrality bill (10/3/2018)
Internet groups urge US court to reinstate ‘net neutrality’ rules (8/27/2018)
Network Neutrality and the Fight to Save the Internet: Background
NSA encryption plan for ‘internet of things’ rejected by international body (5/2018)
Facebook and the Rise of Anti-Social Media: Rob Urie (4/2/2018)
The problem isn’t just Cambridge Analytica or Facebook – it’s “surveillance capitalism” (3/20/2018)
Facebook ordered to stop collecting user data by Belgian court (2/16/2018))
Here Are the 19 Senate Democrats Still Not Committed to Defending Net Neutrality (1/5/2018)
Tim Wu: Why the Courts Will Have to Save Net Neutrality (11/22/2017)
open letter to Google: Stop the censorship of the Internet! (8/28/2017)
Judge orders tech company to release Web user data from anti-Trump website (8/24/2017)
DreamHost is fighting DoJ request for 1.3M IP addresses of visitors to anti-Trump protest site (8/15/2017)
Google Censors Block Access to CounterPunch and Other Progressive Sites (8/9/2017)
Intel's Management Engine is a security hazard, and users need a way to disable it (5/8/2017)
John Oliver's amazing new Net Neutrality video crashed the FCC's website (5/8/2017)
It's a question worth asking: Why is the FCC boss being such a jerk? (4/28/2017)
Facebook Failed to Protect 30 Million Users From Having Their Data Harvested by Trump Campaign Affiliate (3/30/2017)
ISPs and FCC Chair Ajit Pai celebrate death of online privacy rules (3/29/2017)
Ajit Pai, staunch opponent of consumer protection rules, is now FCC chair (1/23/2017)
Fake News in U.S. Election? Elsewhere, That’s Nothing New (11/17/2016)
The problem with the internet is that it shows everyone on earth what they´re missing. David Friedberg quoted in Michael Lewis book: The Fifth Risk.
We’ve ended up with an internet built not for us – but for corporations, political parties, and the state’s increasingly nebulous ‘security’ demands. We need to better understand this problem so that we can challenge it. The problem isn’t just Cambridge Analytica or Facebook – it’s “surveillance capitalism”
"...we've taken the web and we've made Facebook out of it. We put a few profit-motivated men and women in the middle of everything. That was a mistake. Now we're paying for it. We live our social lives, our private lines, in the web and we share everything with our friends, and also with our super-friend, the one who reports to anybody who makes him, who pays him, who helps him or who gives him the 100 billion dollars he desires. We are creating media that consume us, and media loves it." Eben Moglen quoted in Journalism After Snowden.
if we learn only one lesson from the Summer of Snowden, it should be how hostile the Internet has become. Media outlets have repeatedly reported on the insatiable appetite the US government has for the private information of citizens." Ladar Levison
"Why has the invention most celebrated for putting the means of expression in the hands of the people produced a few billionaire moguls and a mass of creative producers expected to work for free ?" Jodi Dean: Democracy and Other Neoliberal Fantasies
"The potential for manipulation and abuse of the digital networks and platforms that citizens have come to depend upon is one of the more insidious threats to democracy in the Internet age. If citizens of established democracies cannot prevent such manipulation, the prospects for aspiring and fragile democracies ... look much less bright." Consent of the Networked: The Worldwide Struggle for Internet Freedom: Rebecca MacKinnon.
The advance of information technology epitomized by Google heralds the death of privacy for most people and shifts the world toward authoritarianism. This is the principal thesis in my book, “Cypherpunks.” Julian Assange: editor in chief of WikiLeaks and author of “Cypherpunks: Freedom and the Future of the Internet.”
"Web 2.0 is a formula to kill the middle class and undo centuries of social progress." Jaron Lanier
"Adding censorship to the Internet means adding surveillance to the Internet. Creating Great Firewalls means creating secret, unaccountable lists of censored material that result in mass abuse, even in the most liberal of democracies. It doesn't matter if you're censoring for copyright infringement or for human-rights reports. The result is the same: a surveillance state." Cory Doctorow: Information Doesn't Want to be Free
"...without congressional action or a strong judicial precedent, I would _strongly_ recommend against anyone trusting their private data to a company with physical ties to the United States. Sincerely, Ladar Levison Owner and Operator, Lavabit LLC" (message announcing the closing of his email business.)
"If the U.S companies and non profits want to support democracy in the Middle East the best they can do is continue to develop a free neutral decentralized internet. Fight the troubling trends emerging in your own backyards from threats to Net neutrality, disregard for user’s privacy, draconian copyright and DRM restrictions, to the troubling trends of censorship through courts in Europe, restrictions on anonymous access and rampant surveillance in the name of combating terrorism or protecting children or fighting hate speech or whatever. You see these trends give our own regimes great excuses for their own actions. You don’t need special programs and projects to help free the Internet in the Middle East. Just keep it free, accessible and affordable on your side and we’ll figure out how to use it, get around restrictions imposed by our governments and innovate and contribute to the network’s growth." Sami Ben Gharbia (2010)
In South Korea, more than half the households are already connected to fiber lines that allow for blazing fast uploads and downloads, and households in Japan and Hong Kong are close behind. In America, only around 7 percent of households have access to fiber, and the service costs six times as much as it does in Hong Kong (and five times as much as it does in Stockholm). Vertically integrated cable companies, whose Internet access product is not provided over fiber and crimps uploads, are well on the way to controlling America's Internet access destiny, having spent millions of dollars over almost fifteen years lobbying against any rules that might have constrained them. (from Susan Crawford's book: Captive Audience)
In 2002 the FCC decided there would be almost no oversight of the broadband highways that deliver the internet to us, believing that the invisible hand of the marketplace would get the job done. Stunningly, the agency actually determined that broadband wasn’t even “telecommunications.” It was instead an “information service,” which meant that consumer protections (like ubiquitous service, reasonable prices, privacy, public safety, and competitive choice) that applied to previous generations’ telephone service would not be required as communications went digital. If consumers wished to enjoy such protections for broadband, they would have to start all over—in a decidedly hostile political and regulatory climate. No other nation allowed such a ludicrous debate over communications semantics to shackle its broadband development. Michael J. Copps 3/2014 CJR
"Don't Panic" Making Progress on the "Going Dark" Debate (2/1/2016)
Powerful NSA hacking tools have been revealed online (8/16/2016)
The
Internet of Things That Talk About You Behind Your Back (1/8/2016)
FTC
Head Calls for Greater Transparency on Data Collected by Internet of
Things (1/6/2016)
NSA Spying Relies on AT&T’s ‘Extreme Willingness to Help’ (8/15/2015)
Ads
Based On Browsing History Are Coming To All Firefox Users
(5/22/2015)
Open Secrets Guide to Net Neutrality (4/2015)
Net
Neutrality: Trade Group Led By AT&T & Verizon Sues FCC
(3/25/2015) Both members of ALEC
The CIA Campaign to Steal Apple’s Secrets (3/10/2015)
Republicans aim to reverse landmark net neutrality ruling (3/6/2015)
Open Internet Survives Weird Politics (3/3/2015)
How the CIA made Google: Inside the secret network behind mass surveillance, endless war, and Skynet— (1/22/2015)
Inside
the NSA's War on Internet Security (12/28/2014)
The
FBI Used the Web’s Favorite Hacking Tool to Unmask Tor Users
(12/16/2014)
Obama Pushes "Open Internet" Policy That Might Benefit People Over Telecoms, Republicans Freak Out (11/11/2014)
The New War Over Net Neutrality (11/10/2014)
Google
is not what it Seems: Assange (10/23/2014)
‘Hostile to privacy’: Snowden urges internet users to get rid of Dropbox (10/12/2014)
Microsoft’s Windows 10 has permission to watch your every move (10/04/2014)
Kremlin
offers Silicon Valley a Russian Internet with Chinese characteristics
(7/5/2014)
This
Is why You Should Delete Facebook Permanently (6/6/2014)
CISCO
CEO Complains About the NSA (5/18/2014)
A Short Guide to the Internet’s Biggest Enemies (3/13/2014)
How the NSA Almost Killed the Internet (1/11/2014)
Where Does Facebook Stop and the NSA Begin? (11/2013)
Lavabit
got order for Snowden’s login info, then gov’t
demanded site’s SSL key (10/2/2013)
Email Service Used by Snowden Shuts Itself Down (8/9/2013)
XKeyscore: NSA tool collects 'nearly everything a user does on the internet (7/31/2013)
Now That It’s in the Broadband Game, Google Flip-Flops on Network Neutrality (7/30/2013)
The Massive On-Line Surveillance no one is talking about (6/10/2013)
Bob
McChesney on Internet Giants and the National Security
State (6/7/2013)
The
Internet Is in Danger of Being Strangled by Commercialism
(4/16/2013)
You
Are What You Click (3/4/2013)
Intel
Will Lead Us To A' La Carte Pay TV (2/22/2013)
The
Inspiring Heroism of AAron Swartz (1/13/2013)
finspy,
the favorite spyware of oppressive governments
everywhere (8/31/2012)
Want
to Pay Less and get more ? (8/1/2012)
Will
ISP's Begin Spying on Users ? (7/6/2012)
The
Net Has Become A Surveillance Machine: Julian Assange
(11/28/2011)
Net Neutrality is Under Attack Again (11/5/2011)
Long Live the Web: Tim Berners-Lee
UN Declares internet access a Human Right
Stand Up Against Internet Censorship (12/7/2010)Waging Peace on the Internet (4/19/2002)
John Oliver on Net Neutrality
Under Obama the FCC ruled for net neutrality Republicans opposed it and with a Republican FCC Chairman overturned it.
‘One Has This Feeling of Having Contributed to Something That’s Gone Very Wrong’
Schrems v. Data Protection Commissioner
US wants free access to your PC (video about 4 minutes.) 6/2010
German government warns against using MS Explorer (1/16/2010)
Imprimatur: How big brother and big media can put the Internet genie back in the bottle.
The US "war on the internet" or this The US "war on the internet"
Internet is Threatened by Censorship, Secret Surveillance, and Cybersecurity Laws.
Support Amnesty International's campaign against Internet censorship.
Why
You Never Really Log Out of Facebook (9/28/2011)
Be Careful what you post on Facebook.
Tim Berners Lee: The Next Web of Open Linked Data (video from Ted talks about 15 minutes)
Top 100 Web Sites from PC Magazine
Public ownership of Broadband is Best
http://www.uruknet.info/index.php?p=m60617
Interested about hacking? Here is a kickstart, go through these materials:https://t.co/VpBBizUcQx
— Jarkko Vesiluoma (@jvesiluoma) April 1, 2020
and then start to practice with reading/hacking:https://t.co/wNrXNWr1Nphttps://t.co/QHQh4JqX6chttps://t.co/opVZMgnv7Nhttps://t.co/wRjBHbsk6zhttps://t.co/U3uTS8jS2p
November 29, 2009
The US "war on the internet" information below is just the tip of
a terrible iceberg, rarely even mentioned, much less examined by
US mainstream media. It is chillingly self-explanatory. In the works
for years, it is being incrementally implemented (for ex., at the
most basic sender-receiver authentication level, as 'anti-spam'.
'anti-ID theft' and other personal 'security' measures.) Total
surveillance and control of information and communications is central
and essential to the phony 'war on terror' --- a state terror war
for global domination as so much of the world on the deadly receiving
end knows. Made clear 'in their own words', even blogging and 'social
networking' are intolerable threats to those in the business of
spreading fear, lies and tyranny.
"The internet needs to be dealt with as if it were an enemy 'weapons
system'..."
Information Operation Roadmap Part 3: "We Must Fight the Net"
A NET OF CONTROL Unthinkable: How the Internet could become a tool
of corporate and government power, based on updates now in the works
Newsweek International Issues 2004 By Steven Levy Picture, if you
will, an information infrastructure that encourages censorship,
surveillance and suppression of the creative impulse. Where anonymity
is outlawed and every penny spent is accounted for. Where the powers
that be can smother subversive (or economically competitive) ideas
in the cradle, and no one can publish even a laundry list without
the imprimatur of Big Brother. Some prognosticators are saying that
such a construct is nearly inevitable. And this infrastructure is
none other than the former paradise of rebels and free-speechers:
the Internet. ... wasnt the Internet supposed to be the defining
example of empowering technology? Freedom was allegedly built into
the very bones of the Internet, designed to withstand nuclear blasts
and dictatorial attempts at control. ...
Certainly John Walker (ed: his important article below) believed
all that. The hackerish founder of the software firm Autodesk..in
the past couple of years noticed a disturbing trend... Walker posted
his fears in a web document called The Dangers of Digital
Imprimatur http://www.fourmilab.ch/documents/digital-imprimatur/
<http://www.fourmilab.ch/documents/digital-imprimatur/> ...(below)
A concurrent step would be the adoption of "trusted computing," a
system by which not only people but computer programs would be
stamped with identifying marks. Those would link with certificates
that determine whether programs are uncorrupted and cleared to run
on your computer. The best-known implementation of this scheme is
the work in progress at Microsoft known as Next Generation Secure
Computing Base (formerly called Palladium)...
article continues following these inserts:
"Trusted Computing"
http://www.youtube.com/watch?v=K1H7omJW4TI
What is TCPA? Why Should You Give a Damn?
http://www.againsttcpa.com/what-is-tcpa.html
Walker isnt the first to warn of this ominous power shift. The
Internets pre-eminent dean of darkness is Lawrence Lessig, the
Stanford University guru of cyberlaw. Beginning with his 1999 book
"Code and Other Laws of Cyberspace,"
Lessig has been predicting that corporate and regulatory pressures
would usurp the open nature of the Net, and now says that he has
little reason to retract his pessimism. Lessig understands that
restrictive copyright and Homeland Security laws give a legal
rationale to "total control," and also knows that it will be sold
to the people as a great way to stop thieves, pirates, malicious
hackers, spammers and child pornographers. "To say we need total
freedom isnt going to win," Lessig says.[...]
US Plans to 'Fight the Net' Revealed by Adam Brookes
http://news.bbc.co.uk/2/hi/americas/4655196.stm January 27, 2006
BBC Pentagon's 2003 "Information Operations Roadmap" newly declassified,
gives a glimpse into the US military's plans for "information
operations" [...]
Secret Pentagon "Roadmap"
National Security Archive Electronic Briefing Book No. 177 A secret
Pentagon "roadmap" on war propaganda, approved by Secretary of
Defense Donald Rumsfeld in October 2003...calls on DoD to enhance
its capabilities in five key Information Operations (IO) areas:
electronic warfare (EW), PSYOP, Operations Security (OPSEC), military
deception and computer network operations (CNO)....
http://www.gwu.edu/%7Ensarchiv/NSAEBB/NSAEBB177/index.htm
Full Spectrum Information Operation Roadmap: Warfare Without Limits
Brent Jessop http://www.knowledgedrivenrevolution.com/Articles/200711/200
71105_IOR_1_Thrust.htm
U.S. Department of Defense Information Operations Related Documents
Information Operations Roadmap (DOD 2003):
Download: http://information-retrieval.info/info_ops_roadmap.pdf
Information Operations (JP 3-13 2006):
Download: http://information-retrieval.info/JP3_13.pdf
Joint Doctrine for Military Deception (JP 3-13.4 2006):
Download: http://information-retrieval.info/JP3_13_4.pdf
Joint Doctrine for PSYOPS (JP 3-53 2003):
Download: http://information-retrieval.info/JP3_53.pdf
Joint Doctrine for Public Affairs (JP 3-61 2005):
Download: http://information-retrieval.info/JP3_61.pdf
Joint Doctrine for Civil Affairs (JP 3-57.1 2003):
Download: http://information-retrieval.info/JP3_57_1.pdf
Joint Doctrine for Electronic Warfare (JP 3-13.1 2007):
Download: http://information-retrieval.info/JP3_13_1.pdf
Information Operations: The Hard Reality of Soft Power, Joint Forces
Staff College and the National Security Agency (2004) (ISBN
1574886991).
America prepares for 'cyber war' with China, Telegraph.uk.co (June
15, 2007).
Pentagon Plans New Arm to Wage Cyberspace Wars
http://www.nytimes.com/2009/05/29/us/politics/29cyber.html?_
r=1&th&emc=th WASHINGTON The Pentagon plans to create a new military
command for cyberspace, administration officials said Thursday,
stepping up preparations by the armed forces to conduct both offensive
and defensive computer warfare.The military command would complement
a civilian effort to be announced by President Obama on Friday that
would overhaul the way the United States safeguards its computer
networks... Officials said that in addition to the unclassified
strategy paper to be released by Mr. Obama on Friday, a classified
set of presidential directives is expected to lay out the militarys
new responsibilities and how it coordinates its mission with that
of the N.S.A., where most of the expertise on digital warfare resides
today...
DARPA, Microsoft, Lockheed team up to reinvent TCP/IP
http://www.theregister.co.uk/2009/10/16/darpa_microsoft_reinvent_internet/
Technology Leaders Favor Online ID Card Over Passwords Michael B.
Jones, Microsofts director of identity partnerships, said...
http://www.nytimes.com/2008/06/24/technology/24card.html?th=
&emc=th&pagewanted=print
Microsoft Palladium: Next Generation Secure Computing Base
http://epic.org/news/2003.html
Today, trackers follow you around the web, skulking in the digital shadows in order to guess what kind of person you are. In Google’s "Privacy Sandbox," your browser will do their job for them. https://t.co/VCCVUfiyn5
— EFF (@EFF) August 31, 2019
Web Content Accessability Guidelines
CISA.gov
Social Media Sites
Social Media
- diaspora*
- Mastodon
- Federation
- FSF on Twitter
- Tumblr
Can you do anything on the web without going through a #BigTech platform?#BigTech gained dominance because the law didn't do its job. So what can you do? Find out in this video!
— FreedomBox (@FreedomBoxFndn) August 2, 2019
"When Antitrust Law Fails: Breaking Up Big Tech with Grassroots Technology"https://t.co/RFZVCj4G6B
http://www.techweb.com/wire/29110640
A Fresh Start for the Internet Stanford University researchers
aren't just dreaming of a new Internet:
they're building it.
"a threat to democracy"
Obama: We Need To Bail Out Newspapers Or Blogs Will Run The World
9-21-09 http://www.businessinsider.com/john-carney-obama-we-need-to-
bailout-newspapers-or-blog-will-run-the-world-2009-9
...<http://www.businessinsider.com/john-carney-obama-we-need-to-bailout-newsp
apers-or-blog-will-run-the-world-2009-9> Obama said he will look
at a news paper bailout, otherwise, blogs will take over the world,
and that would be a threat to democracy bills that could give tax
newspapers tax-breaks if they were to restructure as 50 (c) (3)
educational corporations. One of the bills is that of Senator Ben
Cardin, who has introduced the "Newspaper Revitalization Act
(NB: Bill passed and Obama since has declared a "swine flu" national
emergency) 8/28/9 Bill Would Give President Emergency Control of
Internet http://news.cnet.com/8301-13578_3-10320096-38.html by
Declan McCullagh Internet companies and civil liberties groups were
alarmed this spring when a U.S. Senate bill proposed handing the
White House the power to disconnect private-sector computers from
the Internet. They're not much happier about a revised version that
aides to Sen. Jay Rockefeller, West Virginia Democrat, have spent
months drafting behind closed doors. CNET News has obtained a copy
of the 55-page draft of S.773 (excerpt
<http://www.politechbot.com/docs/rockefeller.revised.cybersec
urity.draft.082709.pdf>
<http://www.politechbot.com/docs/rockefeller.revised.cybersecurity.draft.0827
09.pdf%3E> )...The new version would allow the president to "declare
a cybersecurity emergency" relating to "non-governmental" computer
networks and do what's necessary to respond to the threat. ("Cyber"
is defined as anything having to do with the Internet, telecommunications,
computers, or computer networks.) ...
U.S. Institute of Peace Study by Israeli Professor: Terrorist Groups
Active on the Internet
http://www.dailytimes.com.pk/default.asp?page=story_14-4-200 4_pg7_53
There are hundreds of sites on the Internet serving terrorist groups
and their supporters, according to a study done by the * US Institute of Peace (USIP).
The study undertaken by Gabriel Weimann, a professor at the Haifa
University in Israel and currently a senior fellow at USIP, writes
that today all active terrorist groups have established their
presence on the Internet..
Israeli high-tech companies work for U.S.
U.S. law enforcement wiretaps authorized by the Communications
Assistance for Law Enforcement Act (CALEA)
http://archive.newsmax.com/archives/articles/2001/12/18/2248 26.shtml
[Isreali] Amdocs provides billing and directory assistance for most
American phone companies, Comverse Infosys handles telephone tapping
equipment for US law enforcement, Odigo runs "Instant Message"
systems on computers. All three are closely tied to the Mossad and
the Israeli Defense Force, which is massively funded by u.s. Most
firewalls on US corporate and government computer systems are
provided by Israeli Checkpoint Systems. Odigo's offices near the
World Trade Towers allegedly received two hour advance warning of
the 911attacks...
"From the depth of our heart -- thanks to The Israeli Defense Forces"
Microsoft logo under the text with the Israeli national flag in the
background.
Microsoft CEO: Our company almost as Israeli as American By Maayan
Cohen, TheMarker Correspondent, and Reuters
http://www.haaretz.com/hasen/spages/985800.html Microsoft's Chief
Executive Steve Ballmer, on a visit to Israel... at the inauguration
ceremony of the American software giant's new research and development
center in Herzliya...said Microsoft is an Israeli company almost
as much as it is American...that the proportion of Microsoft employees
per capita in Israel is almost similar to that in the United
States...he knows very few places around the world that offer such
a variety of startup opportunities, and that his company intends
to purchase more Israeli startup companies... the CEO said Microsoft
is not looking to buy all of Yahoo! but is currently engaging in
negotiations about other types of deals with the U.S.
No. 2 search engine.
Related:# Microsoft Israel creating new R&D center in Herzliya #
Yahoo!
President Susan Decker takes interest in Israel # Internet giant
Yahoo! to follow rivals Google, Microsoft to Israel
Emerging Threats Analysis: U.S. military to patrol Internet
http://www.upi.com/Top_News/Special/2008/06/30/Analysis-US-m
ilitary-to-patrol-Internet/UPI-83401214841029/
...<http://www.upi.com/Top_News/Special/2008/06/30/Analysis-US-military-to-pa
trol-Internet/UPI-83401214841029/>
National Dragnet Is a Click Away: Authorities to Gain Fast and
Expansive Access to Records Several thousand law enforcement agencies
are creating the foundation of a domestic intelligence system through
computer networks that analyze vast amounts of police information
to fight crime and root out terror plots.
http://www.washingtonpost.com/wp-dyn/content/article/2008/03
/05/AR200803050366_pf.html
US warrantless wiretapping since 1990s predates 9/11 12/19/07 "The
Register"- Secret surveillance operations that enabled the National
Security Agency (NSA) to access telecommunications traffic data
have been in place since the
1990s....http://www.informationclearinghouse.info/article18928.htm
The Open Source Center is a component of the Office of the Director
of National Intelligence administered by the CIA.
OPEN SOURCE INTELLIGENCE ADVANCES Naquin addressed the Central
Intelligence Retirees' Association October 3, 2007. The text of his
remarks is at http://www.fas.org/irp/eprint/naquin.pdf The DNI Open
Source Center, which gathers, translates, analyzes, and distributes
unclassified open source intelligence from around the world, is
steadily growing in capability and impact, according to Doug Naquin,
the Center's Director. The Open Source Center, which replaced the
CIA's Foreign Broadcast Information Service, is doing more analysis
and outreach than it predecessor and is also exploring new media,
said Mr. Naquin in a recent speech. "We're looking now at YouTube,
which carries some unique and honest-to-goodness intelligence," he
said. "We have groups looking at what they call 'Citizens Media':
people taking pictures with their cell phones and posting them on
the Internet. Then there's Social Media, phenomena like MySpace and
blogs.... A couple years back we identified Iranian blogs as a
phenomenon worthy of more attention, about six months ahead of
anybody else."...
Does The Government Manipulate Social Media?
The U.S. government long ago announced its intention to "fight the
net". As revealed by an official Pentagon report called "Information
Operations Roadmap" (ed: see above) ... "Strategy should be based
on the premise that the Department [of Defense] will 'fight the
net' as it would an enemy weapons system".
CENTCOM announced in 2008 a team of employees would be "[engaging]
bloggers who are posting inaccurate or untrue information, as well
as bloggers who are posting incomplete information." The Air Force
is now also engaging bloggers....
Finally, under the post-9/11 "homeland security" laws, the government
routinely demands full access to ISPs and websites...
Do you doubt that the military and homeland security apparatus would step in to take control of what it considered an "enemy" message? And remember, the government considers any message questioning anything the government does as an enemy message. See this, this, this and this.
this...http://georgewashington2.blogspot.com/2009/01/government-heavily-manipulates-social.htmldigest note re: Soft power propaganda: US/NED/Soros NGO 'pro-democracy'
partner to 'fight terrorism' U.S. government taps Facebook, Google,
MTV to "Fight Terrorism Global Research, November 28, 2008
http://www.globalresearch.ca/index.php?context=va&aid=11198 The US
State Department announced plans on Monday to promote online youth
groups as a new and powerful way to fight crime, political oppression
and terrorism.
Drawing inspiration from a movement against FARC rebels in Colombia,
the State Department is joining forces with Facebook, Google, MTV,
Howcast and others in New York City next week to get the "ball
rolling." It said 17 groups from South Africa, Britain and the
Middle East which have an online presence like the "Million Voices
Against the FARC" will attend a conference at Columbia University
Law School from December 3-5. Observers from seven organizations
that do not have an online presence -- such as groups from Iraq and
Afghanistan -- will attend. There will also be remote participants
from Cuba.
They will forge an "Alliance of Youth Movement," said James Glassman,
under secretary of state for public diplomacy....
"Unless a way of intervening in the radicalization process can be
found, we are condemned to stepping on cockroaches one at a time."
Social Repression and Internet Surveillance: H. Res. 1695, 1955 &
S.1959 By Nikki Alexander
...Jane Harman (D-CA) sponsored H.Res.1955 her partner, Dave Reichert
(R-WA),authored the original bill... H.Res.1695....establishes a
National Commission and Center of so-called "Excellence" to censor
and crush social concerns... perceived to be "threats" by
RAND..."homegrown terrorism,"
"violent radicalization" and "ideologically based violence"...who
have been "violently radicalized" by "extremist belief systems."..."The
Internet has aided in facilitating violent radicalization, ideologically
based violence, and the homegrown terrorism process in the United
States by providing access to broad and constant streams of
terrorist-related propaganda to United States citizens."... RAND
spokesman, Brian Jenkins... said to Jane Harmans Committee: "Unless
a way of intervening in the radicalization process can be found,
we are condemned to stepping on cockroaches one at a time." ...the
precise terminology used by Nazis to justify exterminating
Jews.http://www.informationclearinghouse.info/article18998.htm
The Dangers of Digital Imprimatur
http://www.fourmilab.ch/documents/digital-imprimatur/ by John Walker
Global Internet, Once a spring of liberty, Autumn chill so near.
November 4th, 2003
more at http://www.burbankdigest.com/node/239:
http://www.burbankdigest.com/node/153
___________________________ subscribe mailto:
newslog+subscribe@googlegroups.com<mailto:newslog+subscribe@googlegroups.com>
websites:
http://www.governourselves.org/ http://escapingthematrix.org/
http://thecreditbankdevelopmentmodel.blogspot.com/ http://cyberjournal.org
archives:
http://groups.google.com/group/newslog/topics
http://groups.google.com/group/cyberjournal/topics
Moderator: rkm@quaylargo.com<mailto:rkm@quaylargo.com> (comments
welcome)
What You Can do
Consider writing your legislators.
(Letter to Ct Legislators.)
I am writing to express my hope that you will support town,
city, and county efforts to create municipal high-speed wireless
and broadband networks.
An open Internet, universally accessible, is essential to this
state's educational, informational, economic and cultural future.
But high-speed, broadband Internet access isn't available or
affordable to everyone in our state. That's why many cities across
America are investigating and implementing municipal wireless and
broadband networks. Some are even reducing the cost of deployment
using wireless Internet, known as WiFi, to reach everyone in the
community.
Big telephone and cable companies are trying to stop or slow down
this effort by communities to build municipal broadband and
wireless networks. If they get state legislatures to help them
block competition like they did in Pennsylvania, they could lose an
important incentive to build their networks to connect the
underserved. Municipal wireless and broadband networks could
provide competition to expand availability, lower prices and
improve service. Everyone should be able to connect to the
educational, economic and cultural benefits of the Internet.
Please support efforts to allow towns, cities, and counties to
deploy municipal broadband and wireless networks and resist any
efforts to block their deployment. And as communities explore how
to build universal, affordable, open networks, I also encourage you
to explore partnerships to build upon the skills and expertise of
an experienced telecommunications workforce.
That national security state officials routinely mislead and deceive the public should never have even been in serious doubt in the first place – certainly not for journalists, and especially now after the experience of the Iraq War. That fact — that official pronouncements merit great skepticism rather than reverence — should be (but plainly is not) fundamental to how journalists view the world.
Video
Pay really close attention to this.To Protect and Infect: the Militarization of the Internet. (about an hour.)
Do You Trust This Computer ? (2018) see it on on youtube
Look for other talks by Jacob Applebaum on Youtube.
Bibliography
Network Propaganda: Manipulation, Disinformation, and Radicalization in American Politics by Yochai Benkler, Robert Faris, Hal Roberts
Everybody Lies Big Data, New Data, and What the Internet can tell us about who we really are. Seth Stephens-Dadidowitz
THE DIGITAL REPUBLIC: On Freedom and Democracy in the 21st Century, by Jamie Susskind
2020 United States federal government data breach
The Wealth of Networks, How Social Production Transforms Markets and Freedom by Yochai Benkler has placed the book in the public domain.
System Error: Where Big Tech Went Wrong and How We Can Reboot by Rob Reich, Jeremy Weinstein, Mehran Sahami
THE CONTRARIAN, Peter Thiel and Silicon Valley’s Pursuit of Power By Max Chafkin
Data and Goliath, The Hidden Battles to Collect Your Data and Control Your World: Bruce Schneier
The Ethical Algorithm: Michael Kearns and Aaron Roth
UNCANNY VALLEY: A Memoir By Anna Wiener
Cypherpunks, Freedom and the Future of the Internet: Julian Assange With JACOB
APPELBAUM, ANDY MÜLLER-MAGUHN and JÉRÉMIE ZIMMERMANN
The Big Nine: Amy Webb
The Internet is Not the Answer: Andrew Keen
The People's Platform, Taking Back Culture in the Digital Age: Astra Taylor
No Place To Hide:Glenn Greenwald (Download it for free.)
Digital Disconnect: Robert McChesney
Captive Audience: Susan Crawford
The Master Switch: Tim Wu
The
Future of the Internet and how to stop it: Jonathan Zittrain
Consent of the
Networked: Rebecca Mackinnon
The Filter Bubble: Eli Pariser
Access Denied: Ronald Deibart
Republic.com 2.0: Cass Sunstein
Code and Other Laws of Cyberspace: Lawrence Lessig
Preparing Web Graphics: Lynda Weinman

